Cryptography is the study of data security through Encryption technique, which describe the encryption process and techniques used.
A cipher is an algorithm which is used to encrypt or decrypt the data. Plain text is converted in cipher text with help of this. The transforming process is performed using a key.
This key is like a pattern to encrypt the data. If we wanted to decrypt the data then we need to reverse the process.
Example:
Consider A is represented as D, and B is represented as E, it means all alphabets are replaced with the third subsequent alphabet. Then Apple will be written as:
A = D
P = S
P = S
L = 0
E = H
So, apple in plain text before encryption is APPLE.
This idea or algorithm to replace the alphabet with third subsequent alphabet is known as Cipher.
The third subsequent letter is used to encrypt the data, this secret is considered as a key.
If we want to use this above-mentioned cipher then we must know the rules and the key.
Types of Ciphers in Cryptography
Mainly there are two types of Cipher as given below:
- Block Ciphers
- Traditional Ciphers
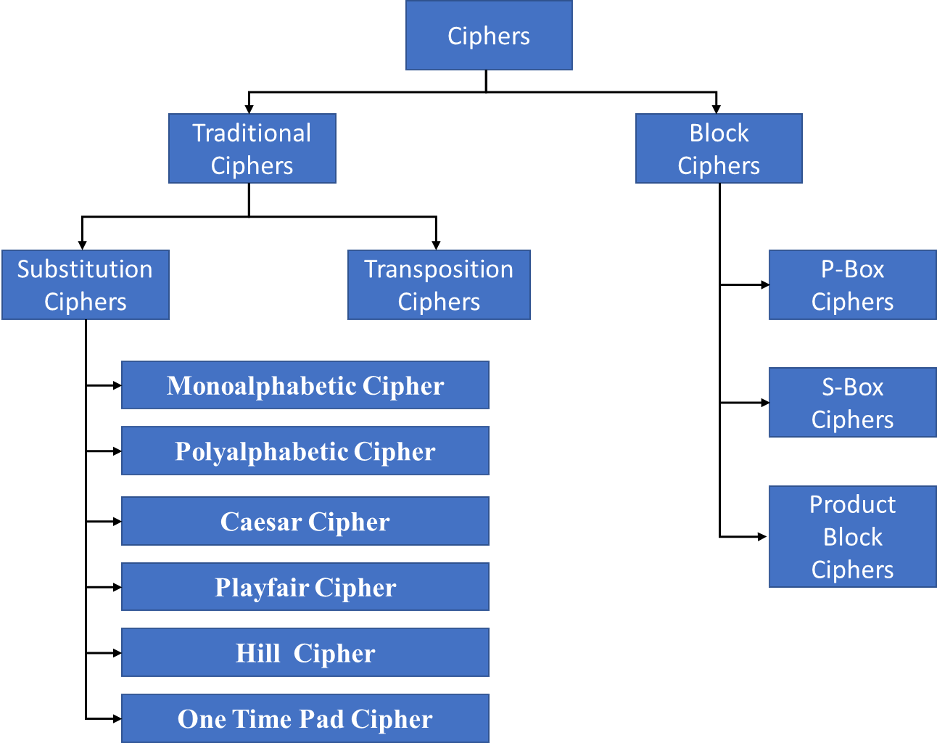
Block Ciphers
These are new technologies. In this a text block is transformed or replaced with a cipher text block instead of single character transformation.
These are again divided in three categories:
- P-Box
- S-Box
- Product Block
P-Box or Permutation Box
Transformation or transposition is performed on bit level.
Plaintext is transformed with digital Bits such as 1 and 0.
The size should be similar in both plain text or cipher text.
S-Box or Substitution Box
Substitution is performed at bit level. It contains three things:
- Decoder: Decoder transform n-bit into 2n bit structure.
- P-Box: P-box perform permutation on this decoded data.
- Encoder: The encoder is used to transform the permuted data into cipher text.
Product Block
If we want more reliable and secure cipher then we can combine P-Box and S-Box to create new cipher, known as Product Block.
It applies both the processing on the plain text for transformation into cipher text.
Also Read: Types of Cryptography
Traditional Ciphers
These are the earlier ciphers. These have simple mechanism. Most of traditional ciphers use single alphabet or character as a unit for transformation. Means one plain text alphabet is replaced with one cipher text alphabet.
These are again divided in two categories:
- Substitution Cipher
- Transposition Cipher
Substitution Ciphers
As name implies the current letter, character, alphabet, number, bit is replaced by some other letter, character, alphabet, number, bit as well. The replacement maybe applied on a single character or a block of characters. let’s look at their sub parts:
1. Monoalphabetic Cipher
Single character is replaced with single alternate character throughout the whole data set. For example, if for a particular data set A is considered as H, then at everyplace letter A is used, that will be replaced with H.
This is an easy method but to find the key is very difficult so this is a good cipher.
Even we can arrange the whole alphabet set to new alternate values as given below:
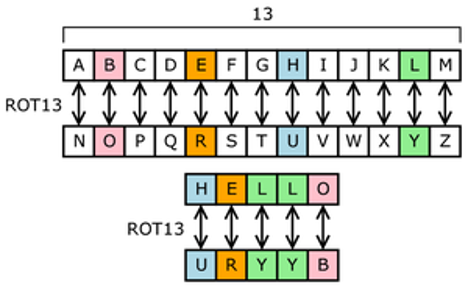
Example:
Plain text: Cipher is an algorithm.
Cipher text: PVCUREVFNANYTBEVGUZ.
2. Polyalphabetic Cipher
In this Vigenere square or Vigenere table is used.
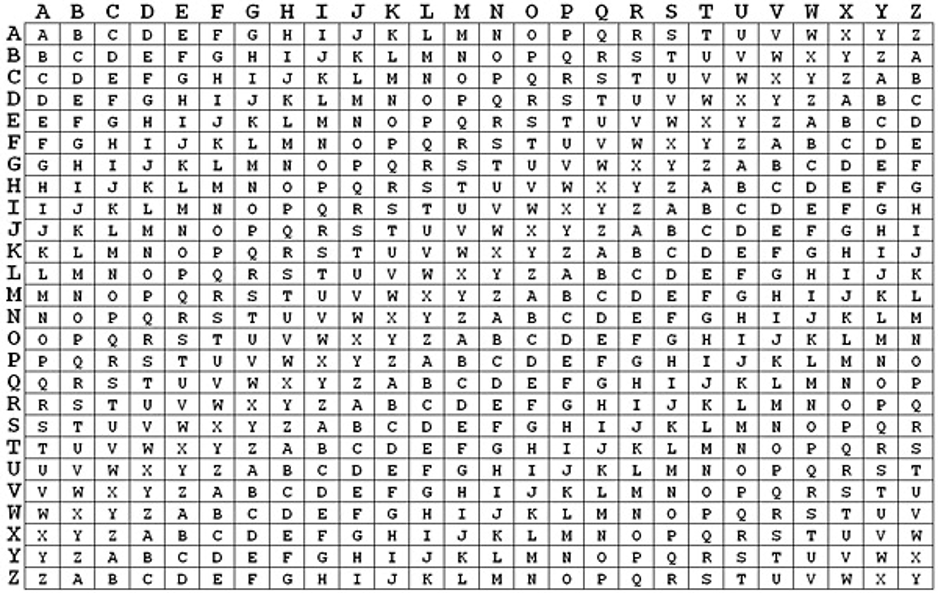
In this table multiple alternates are existing for single character.
The final alternate is depending on the character and the keyword to encrypt the text.
for transformation a key is also used and this key is different for each dataset.
For example, take a plain text APPLE and the keyword is RIGHT, so now A is used with R, P is used with I, second P is used with G, L is used with H, and E is used with T.
A = R
P = I
P = G
L = H
E = T
Now for convert A go for row A and column R. the cross value is R.
Now repeat the process for all the alphabets so the values are:
A = R
P = X
P = V
L = S
E = X

So, Apple is encrypted as RXVSX.
3. Caesar Cipher
This is very simple. In this each alphabet is replaced with its upcoming third subsequent alphabet.
Example: A is replaced by D, B is replaced by E etc.
let’s transform word Cipher:
C = F
I = L
P = S
H = K
E = H
R = U
So, Cipher is transformed in FLSKHU.
4. Playfair Cipher
In this a Playfair square is used, which is 5 X 5 in size.
Steps are as follows:
- First choose a keyword of your own choice. For example, choose “cipherincryptography” (cipher in cryptography)
- Now enter the characters in the 5 X 5 matrix.
- Avoid the repeated word.
- Fill I and J in one cell.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
- Enter the keyword “cipherincryptography”
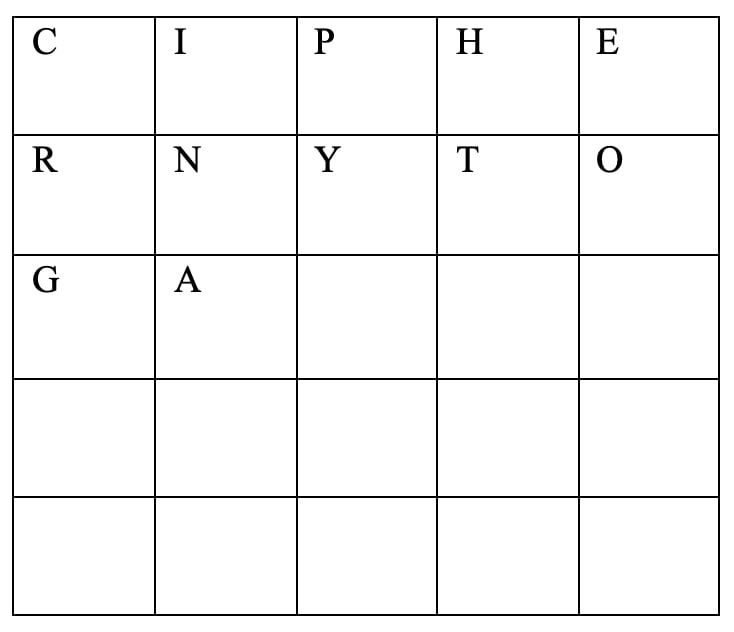
- Now enter the remaining alphabets from A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
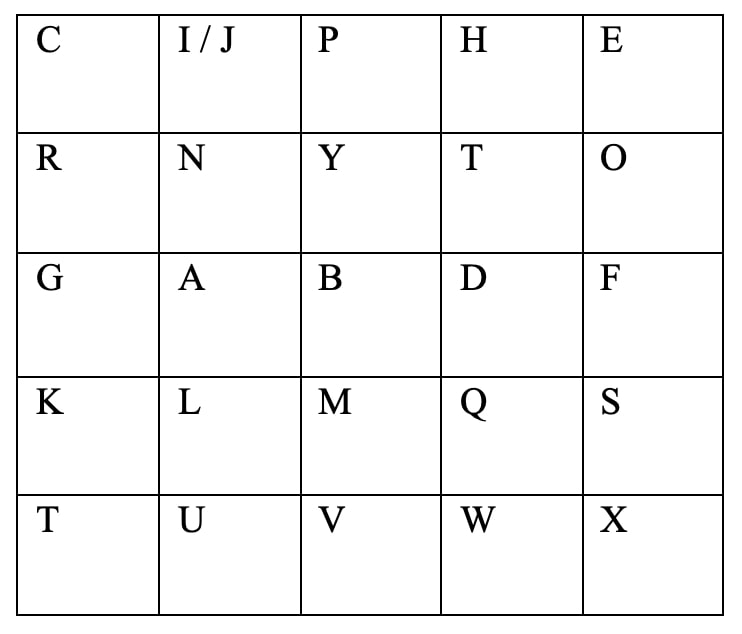
- Now the matrix is ready.
- For transformation follow the rules:
- Break the given words in alphabet sets. Each set should have 2 alphabets.
- If in any set both alphabets are similar then write the alphabet one time and add X.
- If a single letter is existed then add Z.
- If both alphabets are available in same row, then replace them with their just next right alphabet.
- If both alphabets are available in same column, then replace them with their just next below alphabet.
- If both alphabets are not in same row or same column then swap them with their just right or left alphabets but with other corner of the cube.
For example, choose word Apple:
Apple = AP PL EZ
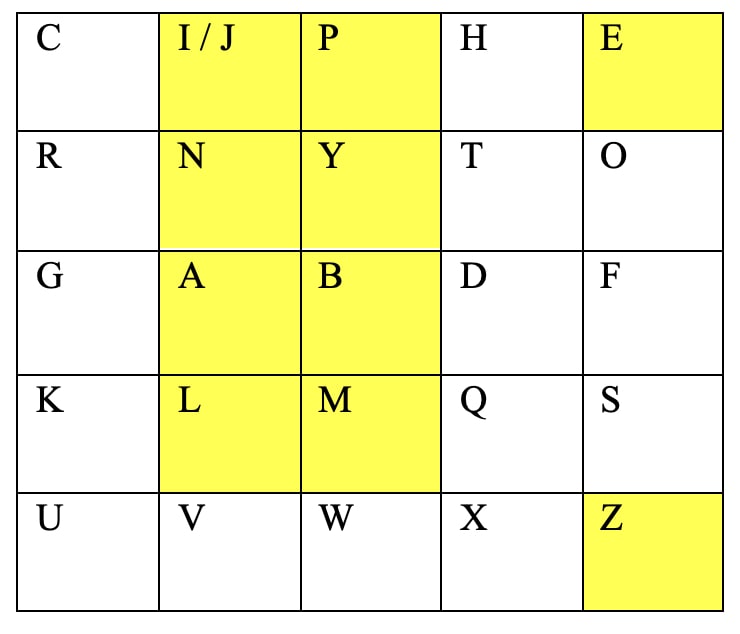
AP = BI (We can choose any either I or J)
PL = IM
EZ = OE
So, Apple is encrypted as BIIMOE.
5. Hill Cipher
This is a complex mathematical algorithm to encrypt the data.
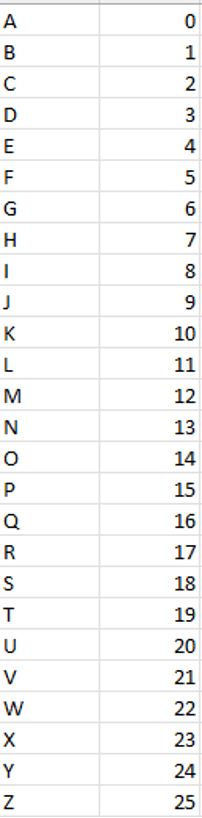
- First apply numbers to alphabets such as:
- Then choose a key matrix (m*n) size.
- Then choose the word to encrypt.
- Break the word in size equal to key matrix.
- Now convert the word matrix in number matrix.
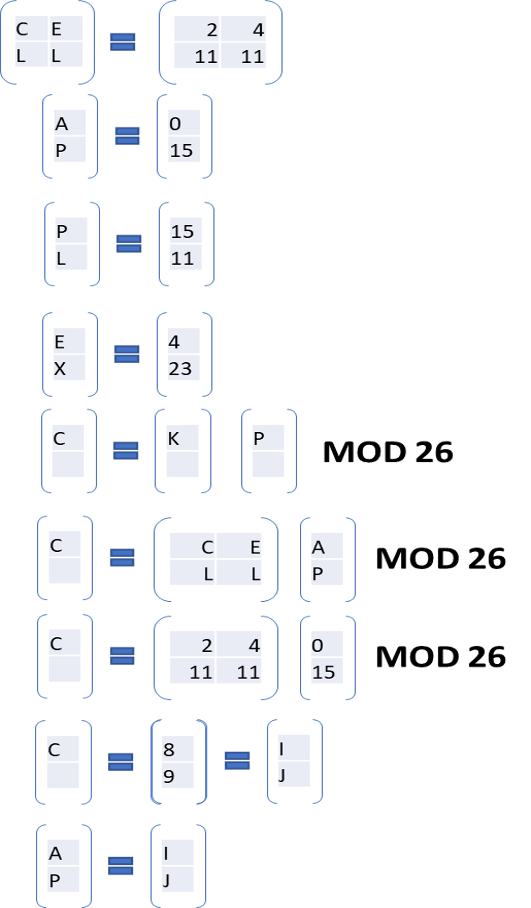
- Now find the cipher matrix by using this formula:
- C = KP mod 26
Here C = cipher matrix
K = key matrix.
P = word matrix
- now transform the cipher matrix into word matrix.
- Follow the process for the whole data set.
Example: We choose word Apple to transform. Convert the alphabets into numbers from the above-mentioned table.
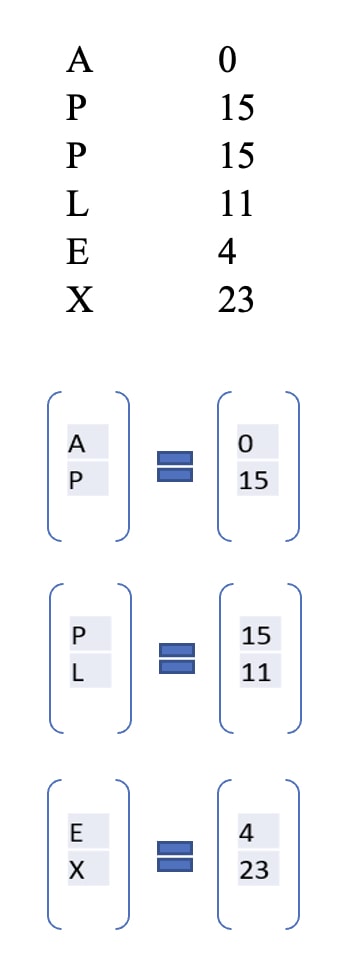
The size of word matrix is equal to the size of key matrix. Hence 1 X 2.
Now choose a keyword:
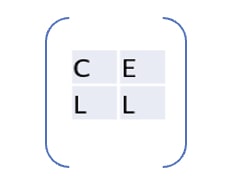
We choose CELL as key word.
Plot it in matrix. Cell has four characters so the matrix will be 2 X 2 in size as given:
Now convert it into number matrix:
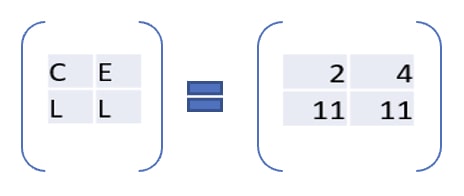
Repeat the process for other two word matrix.
The final transformation will be look like this:
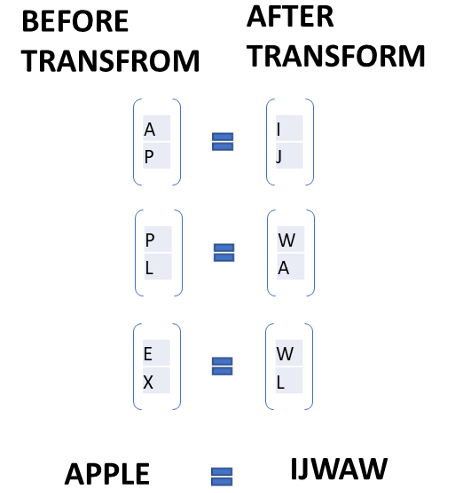
So, this is the method of Hill cipher. It’s quite lengthy and complex.
6. One-time Pad
It is similar like substitution cipher but here original alphabets are replaced with the same size keyword. Means size of plain text and keyword is similar. The keywords are generated on random basis. Each keyword used once only.
It is impossible to crack the code due to multiple combinations.
Transposition Cipher
In this the order of the given word is being changed. The given words are placed in a m*n matrix, and then the alphabets are replaced with the subsequent alphabet. The interval is chosen as per the key.
For example:
Transposition cipher is tough and the secret random key chosen is 6. Now create a matrix with 6 column and required rows.
And place the given string in it.
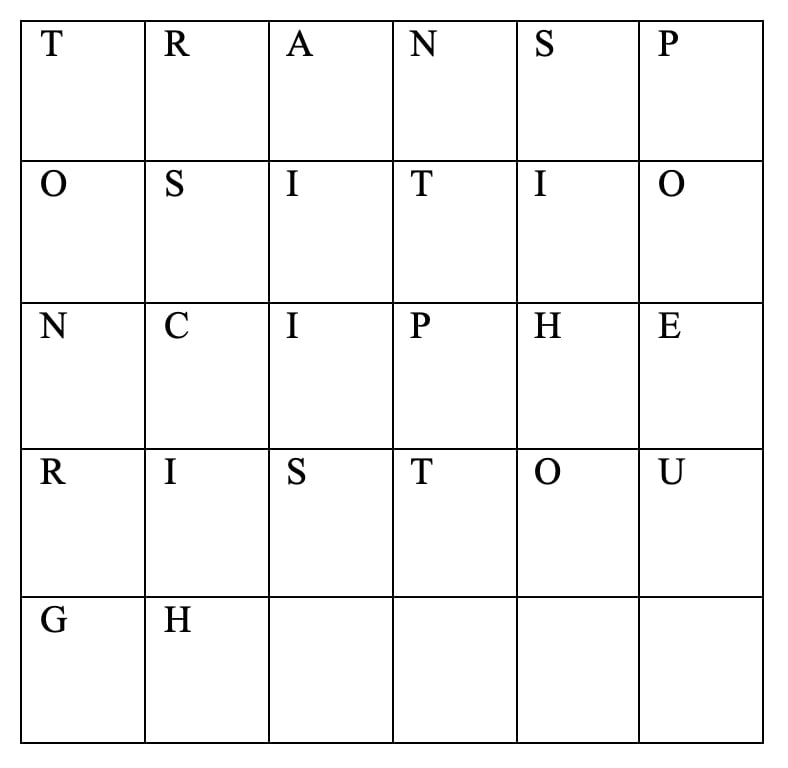
Now our key is 6, so replace T with subsequent 6 alphabet in the given matrix.
So, T = O
Now change the whole string with the same procedure.
Plain Text Cipher Text
Transposition cipher is tough = OSITIONCIPHERISTOUGHTRANSP
Additional Ciphers
1. Polygraphic Cipher
It is similar as substitute cipher, but in this plain text blocks are replaced with cipher text blocks instead of individual letters or characters.
The plain text is divided in larger groups. Each group is replaced with same size cipher text block.
Playfair and Hill cipher are the example.
2. Permutation Ciphers
This is quite opposite of substitute ciphers. In this the plaintext is rearranged in any possible order.
Permutation simple means rearrange the order of characters and alphabets in plain text.
Example:
Hey is a plaintext. Now find its permutations:
H E Y are three letters so number of total possible permutation is:
3 X 2 X 1 = 6
So, let’s find these 6 permutations manually by rearrange the order.
- Hey
- Eyh
- Yhe
- Hye
- Ehy
- Yeh
Now we can use any permutation instead of Hey. This is permutation cipher.
3. Private-key Cryptography
In this method a Private key is used for encryption and decryption.
This key should be same for the encryption or decryption of the same text or data.
This key is shared between the sender and receiver of the text.
4. Public-key Cryptography
In this method two different keys are used for encryption and decryption.
First key is used to encrypt the plain text into cipher text. This key is called the Public key.
Second key is used to decrypt the cipher text into plain text. This key is called private key.
Here we tried to cover all popular types of ciphers in cryptography. In case you have any queries or suggestions please mention in the comment section below.
The post Types of Ciphers in Cryptography appeared first on The Crazy Programmer.
from The Crazy Programmer https://ift.tt/Hv29i1l
Comments
Post a Comment