Cybercriminals are acknowledging package sniffing attacks to steal customers’ data. These attacks are a significant threat to cyber security. Packet sniffing is a crucial thing in network management. And network managers use the practices of sniffers to analyze the threats or any underlying technical issues.
However, now cybercriminals are also using this strategy to conduct illegal activities. Hence, it is crucial to understand packet sniffing attacks in detail. Thus, in this article, we will analyze what package sniffing attacks and their other aspects are. Therefore, stick to this crucial article if you belong to the IT industry or are interested in knowing the same.
What is Packet Sniffing Attack?
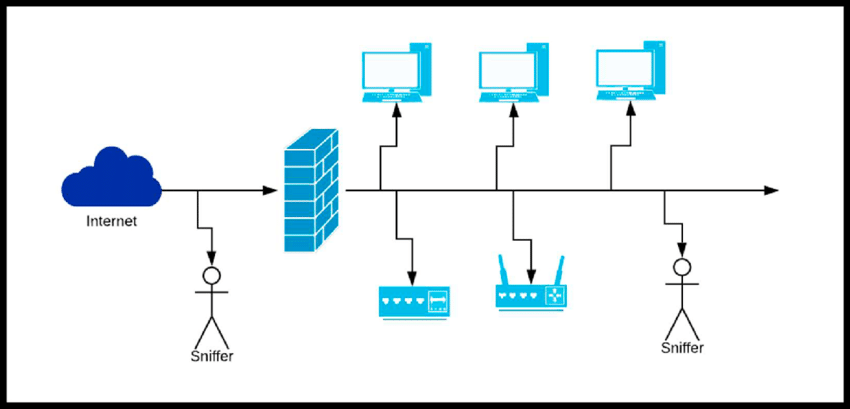
Packet sniffing attack is checking and analyzing the data packets that pass through the network. And these packets are mainly moved over the network using sniffing, which is a specialized tool. The data can contain information about wealth or other information, all of which are in data packets. And these packets proceed inbound or outbound traffic.
However, the sniffing attack takes place when the cybercriminals execute criminal activities using this technique. In this, they extract the packet data by making it unencrypted when it passes through the network. In short, these are cybercrimes where the criminal captures the traffic using packet sniffers. And by doing this, they extract all unencrypted data from the packets.
Therefore, if any organization gets caused by sniffing attacks, they can meet significant loss. Hence, it is essential to use best practices to prevent packet sniffing attacks.
Legal and Illegal Use of Packet Sniffers
There can be legal and illegal use of packet sniffers by the IT professional. When IT professionals and networking experts use packet sniffers to analyze traffic and security analysis, it’s called legal packet sniffers. And by using it, they can find the troubleshooting network issue of the organization as well.
It can also be used for the information security context. However, this tool can also be misused if the wrong person gets such tactics. Sniffing tools can be illegally used for stealing the data of customers. It can discover the passwords and bank details of the user as well. The hackers can also execute other malicious activity using sniffers.
Some packet sniffer tools are BetterCAP, WinDump, Wireshark, and Ettercap. Most people do not know sniffer attacks can cause them if they use an unsecured WiFi connection. By using such tools, the hackers can execute DDoS or MitM attacks as well. Hence, these factors must be considered because they can be a threat to businesses.
Are Packet Sniffing and Spoofing Both Same?
Most of you may not know that spoofing and sniffing are different. Mainly these two phrases are used interchangeably among businesses. But both are entirely different from each other because sniffing has the direct involvement of the hackers. Because here, hackers intercept the network to obstruct traffic and gather unencrypted data.
Whereas in spoofing, there is no direct involvement other than the man in the middle attack. In this method, the hacker impersonates the other person to execute the same malicious goal. They intercept the traffic having packets and gain access to the targeted or sensitive data of the organization.
Types of Packet Sniffing Attacks
There are mainly two types of packet sniffing attacks such as mentioned below.
1. Active Packet Sniffing Attack
An active packet sniffing attack is a cyber-attack where hackers manipulate the switch-based network. And nowadays, most networking components are switch-based, and they connect with sports. Hence, by using switches, they forward the data to other predefined ports to control the port’s MAC. Here MAC represents the media access control of the port connected to pass the data. Some common examples of active sniffing attacks are MAC fooling, ARP spoofing, and DNS spoofing.
2. Passive Packet Sniffing Attack
The cyberattack takes place by using a bunch of networks, and here hackers use MAC addresses to understand the destination port of the data. Here you will not see any direct connection with the target as like an active sniffing attack. Therefore, these attacks are complex to detect and prevent because these attacks are passive in nature.
How to Prevent Packet Sniffing Attack?
There are many preventative ways to stay away from packet sniffing attacks. However, these methods do not guarantee but help you build a healthy ecosystem to secure your organization; sensitive data.
1. Prevent Using Unsecured Networks
Have you ever heard bank data has leaked and the user lost his credit card details? These are general examples of packet sniffing attacks. And mostly, it happens because such users use unsecured WiFi networks. Also, such hackers or attackers may use the vulnerable network for installing their offers to monitor, analyze, ready, and steal the data. Many hackers also create fake public WiFi networks to harm innocent people by getting their sensitive data. Therefore, it is crucial to avoid using unsecured WiFi networks because they may harm you.
2. Start Using Vpn To Make Messages Encrypted
Mostly, attackers gather unencrypted data from the network’s traffic. Hence, if you want the most effective way to prevent sniffing attacks, you should use VPNs to make your organization’s message encrypted. It will help you to enhance your virtual privacy and also prevent cyber attacks on your device. Therefore you can also consider using a virtual private network or VPN for your organization’s devices.
3. Use Networking Monitoring and Scanning Activities
You can also hire network administrators and IT professionals. They will scan and monitor the data traffic that happens from the network. Also, they will help you by monitoring the bandwidth and device auditing to find any suspicious thing. However, it is a must-use activity for you to secure yourself from sniffing attacks. Because most networks are unsafe and might have some harmful elements. Therefore, with an excellent team of qualified, ethical hackers and IT professionals. You can make more secure network strategies to keep your and your customer’s data safe.
So, these are just a few ways to prevent sniffing attacks in your organizations. However, there might be some other ways, but these three are crucial to implementing.
Conclusion
Now you know “what is package sniffing attack,” and you also have learned its types with examples. Now only sniffing attack types, we also discussed ways to prevent sniffing attacks. Hence, we hope you liked this great post and shared it with your friends as well. If you keep wanting to learn such excellent technical terms in a simplified manner. You can stay tuned with our blog and another post as well. So, let’s know your thoughts on the package sniffing attack in the comment box.
The post What is Packet Sniffing Attack? – Types and How to Prevent It? appeared first on The Crazy Programmer.
from The Crazy Programmer https://ift.tt/3Dz2uwg
Comments
Post a Comment