What is Intrusion Detection System (IDS) – Working, Types, Best Tools Neeraj Mishra The Crazy Programmer
Have you ever wondered how much data is available on the internet? Although there can never be an actual figure of the amount of data available online, the internet holds tonnes of sensitive data. Such data is valuable to intruders and malicious actors who are ready to do anything to lay their hand on the data.
Indeed, cases of data breaches have been increasing, and so has the cost of data breaches. Therefore, the data needs to be protected at all costs. You might already know of some of the data protection tools and measures. For instance, you might have heard of SSL certificates that are essential in data encryption. They encrypt the exchanged communications between the web browser and the client-server and keep away hackers and sniffers.
Today, several trusted and inexpensive SSL certificates exist, such as Comodo PositiveSSL certificates and RapidSSL certificates. The predominance of SSL certs makes them the most popular and effective data protection tools. However, SSL certificates are a topic for another day. Today, we will pay much attention to another critical data protection system- An intrusion detection system. We will begin by defining what an intrusion detection system is.
What is Intrusion Detection System (IDS)
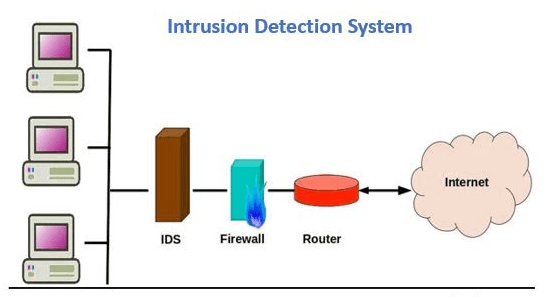
An intrusion detection system refers to a special kind of software specifically designed to keep an eye on the network traffic to discover system irregularities. These malicious network activities could mean the beginning of a data breach or the end of one. Therefore, the primary purpose of an intrusion detection system is to detect network anomalies and report on the said anomalies. Please note that the intrusion detection system does not prevent threats from happening, unlike the intrusion prevention system.
How Does Intrusion Detection System Work?
As I mentioned earlier, the primary purpose of an intrusion detection system is to detect network anomalies to catch attackers before they carry out real damage to a network. An intrusion detection system may be host-based or network-based. As the names suggest, a network-based intrusion detection system resides on the network, whereas the host-based intrusion detection system resides on the client computer.
The IDS works by looking for the signatures of known attacks. They also analyze system functionalities to spot any deviations, and such deviations will be inspected at the protocol layer. In the past, intrusion detection systems have proven effective in detecting threats such as Domain Name System poisoning and Christmas tree scans.
Users can implement an intrusion detection system either as a software application or as a network appliance. Additionally, there are cloud-based intrusion detection systems that are specifically meant for cloud-based purposes.
Types of Intrusion Detection Systems
There are several types of intrusion detection systems. Each IDS type uses different methods in detecting suspicious activities. The following are the types of intrusion detection systems that you must know.
- A Network Intrusion Detection System (NIDS) is primarily meant to detect intrusions across an entire network. The NIDS will monitor all incoming and outgoing traffic on all devices across a network and detect anomalies.
- A Host Intrusion Detection System (HIDS) usually detects intrusions through a particular endpoint. For instance, a HIDS will run on all computers and devices across your network. The significant advantage of a host intrusion detection system over a network detection system is that a HIDS can detect abnormal network packets within an organization, which a NIDS might not detect at times. Additionally, a HIDS is capable of identifying malicious traffic originating from the host. For instance, it will notice when a host has been infected with malware and tries to spread the malware across the network.
- A Signature-based Intrusion Detection System (SIDS) keeps an eye on all traffic on a network and compares the traffic against databases of attack signatures or other known cybersecurity risks.
- An Anomaly-based Intrusion Detection System (AIDS) is designed to pinpoint unknown cybersecurity attacks such as novel malware attacks. It will compare the attacks against an established baseline. It uses machine learning techniques to develop a trustworthy activity baseline referred to as a trust model. It will compare the new behaviors to the verified trust models. The major drawback of AIDS is that it can sometimes raise a false alarm whenever previously unknown but legitimate network traffic is identified as an anomalous activity.
5 Best Intrusion Detection System (IDS) Tools
There are multiple IDS tools, but the following are the most reliable ones.
1. SolarWinds Security Event Manager
The SolarWinds Security Event Manager is one of the best IDS tools. It came top on the list of the best IDS tools because of its ability to integrate real-time log data across an organization’s infrastructure. As such, the SolarWinds security event manager can operate both as a Network intrusion detection system (NIDS) and A host-based intrusion detection system (HIDS). This ability makes it the most effective IDS tool since it can detect various malicious attacks and protect your system against security threats. Moreover, the SEM tool is created to employ both anomaly-based and signature-based intrusion detection techniques.
It achieves this by making a comparison of network traffic sequences against a set of customized rules. In addition, it allows users to conduct high-level intrusion detection on all types of devices and operating systems such as Windows, macOS devices, and Linux. The SEM tool is thus a robust intrusion detection system tool that will perfectly fit your organizations’ needs.
2. McAfee
McAfee is another great IDS tool specifically designed to give real-time risk awareness to both virtual and physical networks. It applies signature-based and anomaly-based intrusion prevention techniques. Additionally, it uses the emulation approach in detecting and identifying malicious activities and security threats.
Even more interesting with this IDS tool is its ability to correlate threat activity with application usage. This ability makes it easy for the tool to prevent network issues arising from cyber breaches. The McAfee IDS tool also uses an SSL certificate to encrypt inbound and outbound data.
But the fundamental advantage of the McAfee IDS tool is its integrability and scalability features. The features allow you to develop your virtual workloads and join other McAfee platforms to receive more advanced threat and antivirus protection.
3. Suricata
Suricata is a free IDS tool. It operates on a code-based platform. It is primarily designed on a signature-based intrusion detection system to detect real-time cybersecurity threats and other malicious system anomalies. The tool will thus allow to quickly counter-attack impending cyber-attacks. The tool is also built to examine multi-gigabyte traffic and to routinely detect protocols. Its machine learning and artificial intelligence capabilities make it easy for the tool to determine normal behavior from irregular behavior.
However, although the Suricata IDS tool is a great free option to detect system anomalies, its lack of documentation capabilities has been its major flaw. As such, the tool can be a victim of troubleshooting issues, and it can be challenging for users to keep track of its operations by referencing the past and preparing for the future.
4. Blumira
Blumira is a security information and event management IDS tool primarily created to detect threats in on-premises and cloud-based premises. It is an effective tool since it continually monitors your IT infrastructure to detect malicious activities and misconfigurations. Such threats could lead to data leaks and compliance breaches. It allows to respond to an ongoing attack swiftly and to stop attackers in their tracks.
With Blumira, you can customize your intrusion detection reports and also automate their options. It is also known for its easy-to-use and straightforward user interface.
5. Cisco Stealthwatch
The Cisco Stealthwatch is an enterprise-based network intrusion detection system and host intrusion detection system. It is an excellent IDS tool to scale your business requirements. It leverages a scalable intrusion detection system that will make you well-prepared to adopt the intrusion prevention tactics that are on the rise. It is also an excellent tool because it can detect malware in an encrypted network without necessarily decrypting the network.
Conclusion
An IDS is a vital element in protecting both on-premises and cloud-based IT environments from cybersecurity threats. There are several intrusion detection systems available today, which you can choose to work with. This article has listed the top five dedicated intrusion detection systems, and it has also explained what intrusion detection is and some of the types of IDS.
The post What is Intrusion Detection System (IDS) – Working, Types, Best Tools appeared first on The Crazy Programmer.
from The Crazy Programmer https://ift.tt/3n2aEIq
Comments
Post a Comment