Credential Stuffing Attacks – Definition, Detection and Prevention Neeraj Mishra The Crazy Programmer
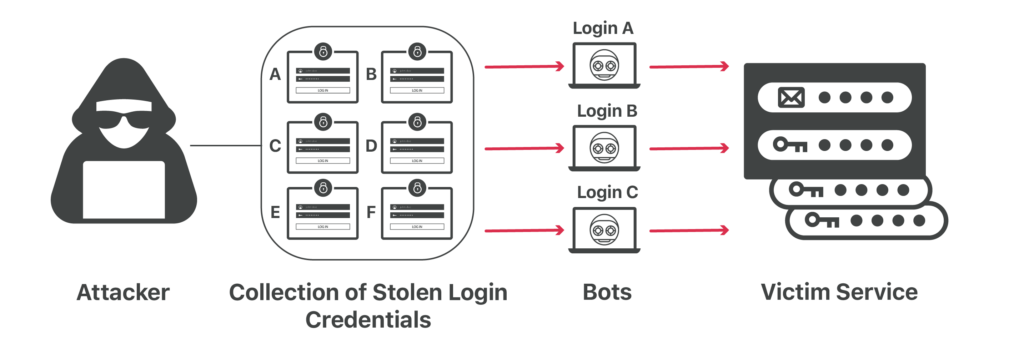
A credential stuffing attack is a cybercrime technique where attackers use automated scripts and try them on a targeted website. It happens because the majority of users repeat similar credentials on more than one account. That means one data threat can also threaten several others. The attackers use tools like Sentry MBA to test such certificates in the highly automated bulk effort. Sometimes theft succeeds in login in allowing them to take advantage of services, stored credit card numbers, and other personal information.
The attackers inject username and password pairs to try unauthorized access to user accounts. Therefore, organizations need to stress the importance of using different passwords if one has more than one account. Using duplicate passwords for different accounts can be hazardous because once the hackers get to know one of the passwords; they will get access to any of your other accounts.
When you understand different ways that attackers use to access your business information, you will do everything possible to keep them at bay. Attackers are dangerous to any business as they can use that to bring down your business.
How to Detect Credential Stuffing
You can use multiple ways of detecting credential stuffing that you can apply to prevent any stuffing attack on your business. Here are examples of what you can do to catch the stuffing attack.
Several Login Attempts
Monitor your account and find out whether you can note several login attempts. Most of the multiple attempts happen when someone who is not the account owner tries several login credentials just if one of them will be accepted by the system. It can either be from one endpoint or several endpoints.
Separate IP Addresses
Detect known malicious endpoints attempting to log in using separate IP addresses or fingerprinting techniques. Also, check for automation of software in the login processes. Avoid scenarios where your company’s employees want to use various devices to log in to your system.
Removal Credential Attempt
Look for any attempts to remove credential-based login and to replace it with password-less authentication.
Tips on Preventing Credential Stuffing Attack
Use the following tips to keep attackers away from using credential stuffing attack on your business:
Multi-Factor Authentication
Multi-factor authentication (MFA) is one of the most effective ways of protecting your credential stuffing. It works by asking users to use additional authentication like using mobile as a defence to credential stuffing. The attacker bots are not capable of providing physical authentication method such as mobile phones. Most of them cannot even work with multiple authentications. Combining your authentication process with other techniques gives the attackers a hard time and prevents credential stuffing attacks.
Use of CAPTCHA
Use of CAPTCHA is another way of making sure the attackers do not access your account. The process of using the CAPTCHA requires users to perform specific actions to prove that they are human. That is an effective way of reducing credential stuffing attacks. However, the CAPTCHA method has limitations and can only be used in specific scenarios.
Use of Email Address
Avoid using email addresses as user IDs as the credential stuffing relies on the reuse of usernames or account IDs. User stuffing attack is most likely when you are using their email address as an account ID. Disallowing email ID is one of the most effective ways of reducing the credential stuffing attack.
The attackers use an account checker to try the stolen credentials on multiple websites like social media or online marketplaces. If the attempt works, the attacker can match different accounts with the stolen credentials. That is a quick way of draining the stolen account of any stored value like the credit card numbers or any other personally identifiable information. Using the stolen credentials, the attacker can create other transactions.
How to Use Imperva Bot Management as a Preventive Measure for Credential Stuffing Attacks
Imperva provides multi-layered protection to ensure that websites and applications are available and easy to access and keep them safe. The Imp[erva application works in the following ways:
DDoS Protection
DDoS maintains uptime in all cases preventing any type of DDoS attack by hindering access to your website and network infrastructure. Attackers can use your downtime to attack your accounts.
CDN Protection
CDN enhances website performance while reducing bandwidth costs with CDN-designed developers. You can also accelerate APIs and dynamic websites. It is essential to make sure that your business is protected at all times from any form of credential attacks.
WAF
Cloud-based solutions are effective in permitting traffic and preventing bad traffic, thus safeguarding applications at the edge. The best thing with is that it keeps applications and APIs in your network safe.
API Security
The IPS security is essential for protecting APIs by ensuring only the desired traffic can access your endpoint and keep everybody else away. It also detects and blocks your website from exploits of vulnerability.
There are several other methods of protecting the credential stuffing of your account. However, it is essential to make sure that you use the most effective and easy-to-use method. Sometimes it calls for multiple prevention measures just to make sure that you are completely protected. Your business needs proper protection from the credential stuffing attack as well as all the other cybersecurity attacks. Cybersecurity is critical for every business as a breach of security can break your business.
Regardless of the method you choose to protect your business, one most effective prevention method is making sure the employees are well trained. It is essential to train the staff and make sure they understand the effect of cyber attacks and how they can change everything in your business. Attackers can bring down your business in different ways.
They can steal not only important information but also business valuables like transferring money from accounts. They can also bring your business down by tinting your reputation. When customers and suppliers hear that you have been attacked, they will lose confidence in you and eventually limit their transactions with you. That will be the beginning of your business downfall and can lead to a collapse of your business.
The post Credential Stuffing Attacks – Definition, Detection and Prevention appeared first on The Crazy Programmer.
from The Crazy Programmer https://ift.tt/3rtHVvb
Comments
Post a Comment