Spyse is a relatively new service in cybersecurity, but their innovative approaches have gained the attention of many pentesters and cybersecurity specialists.
The service itself is a cybersecurity search engine which can be used for gathering mass technical data from the internet. The special thing about Spyse, is that they have one of the largest databases of its kind: hosting all the technical internet data that specialists might need for finding vulnerabilities, gathering competitor data, or just overall reconnaissance.
Read on to learn how they collect, store, and provide the data.
How Spyse Collects Data Globally
Spyse engine performs regular data scans all over the world. This is done thanks to a global server distribution system, which not only lets them bypass area scanning restrictions and ISP blocking, but enables them to harvest much more data from their sources than you would normally get.
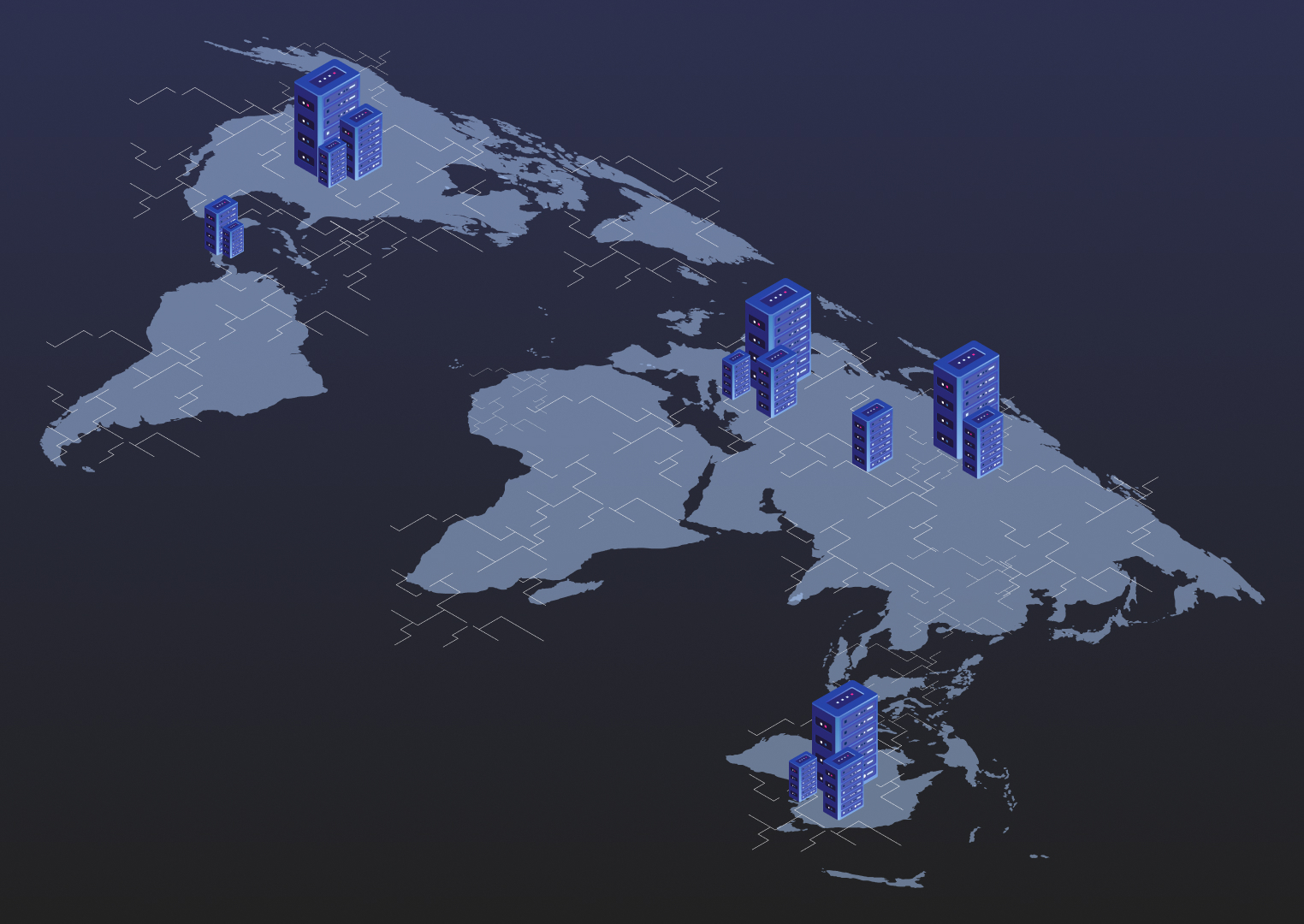
Their scanning infrastructure is composed of ten self-developed scanners. Each of these scanners focuses on collecting specific types of information. After the data is gathered, it gets processed by sorting algorithms and stored into the Spyse database.
Database Browsing
The database has all the data users would need for reconnaissance stored and instantly available. Not only that, but searching for data lets users see interlinked, or connected results. This makes for more browsing opportunities like gaining extra information on targets, seeing more vectors of attack, even visualizing tech-data relationships between different companies.
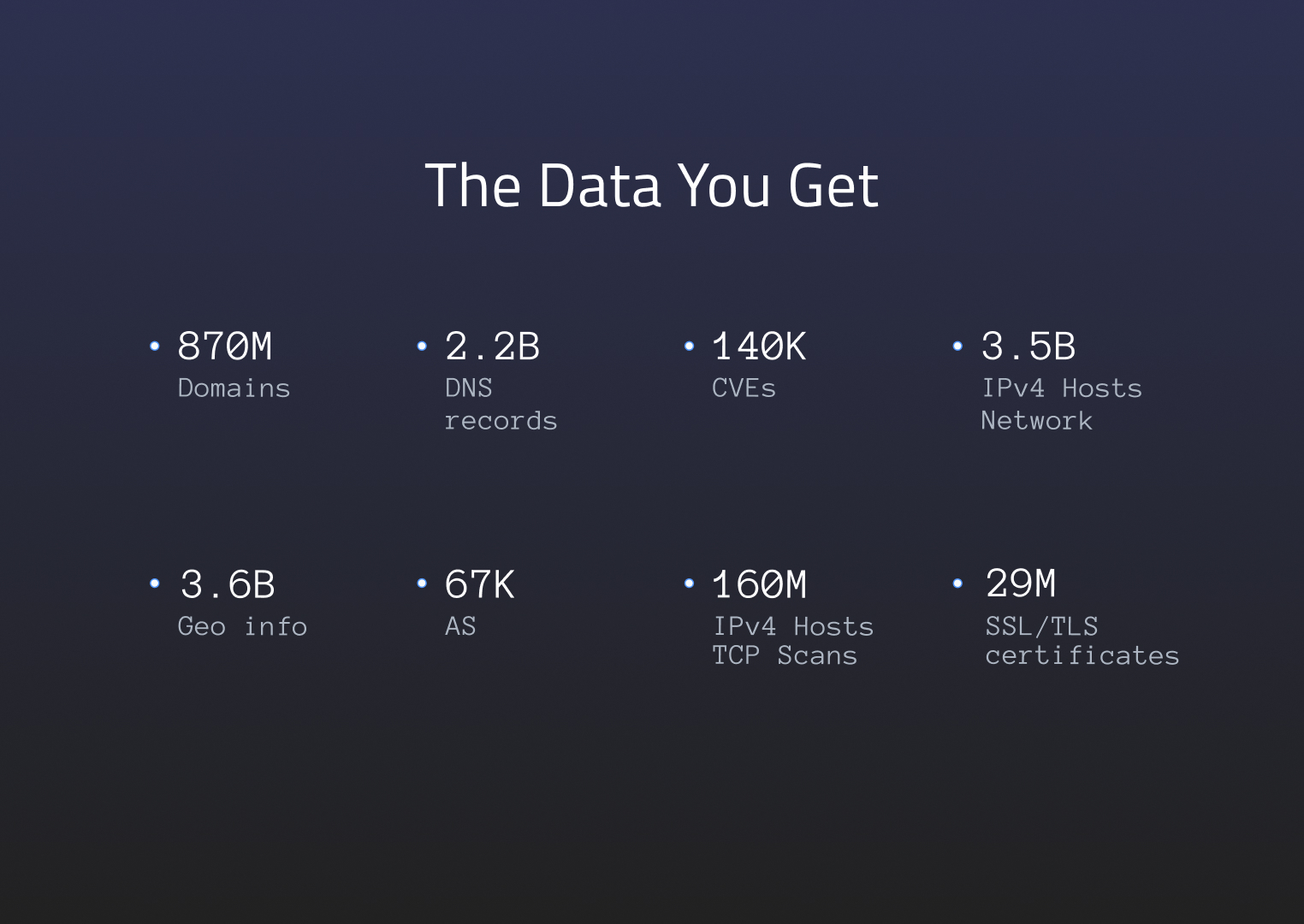
The database itself stores over 7 billion documents of hot data on 50 high-functioning and most reliable servers. This data contains everything: DNS records, SSL/TLS certificate data, domains and subdomains of various organizations, IP data, and much more. The biggest perk is the fact that you can access all of it instantly, without having to wait for scans.
Web Interface, API, Python
Spyse can be accessed through a web interface and an API.
The web interface looks like a familiar search engine perked for cybersecurity. Search results return in tables which can then be filtered to get a more convenient look. All found results can then be downloaded and accessed offline.
Alternatively, users can use this search engine via flexible API or integrate it with their tools and services. API has a documentation on Swagger, which makes it a pleasure to work with. It’s flexible, and can be used with many methods which are outlined on the API documentation.
Extra Productivity Tools
There are two handy features that alleviate the utility of this cybersecurity search engine.
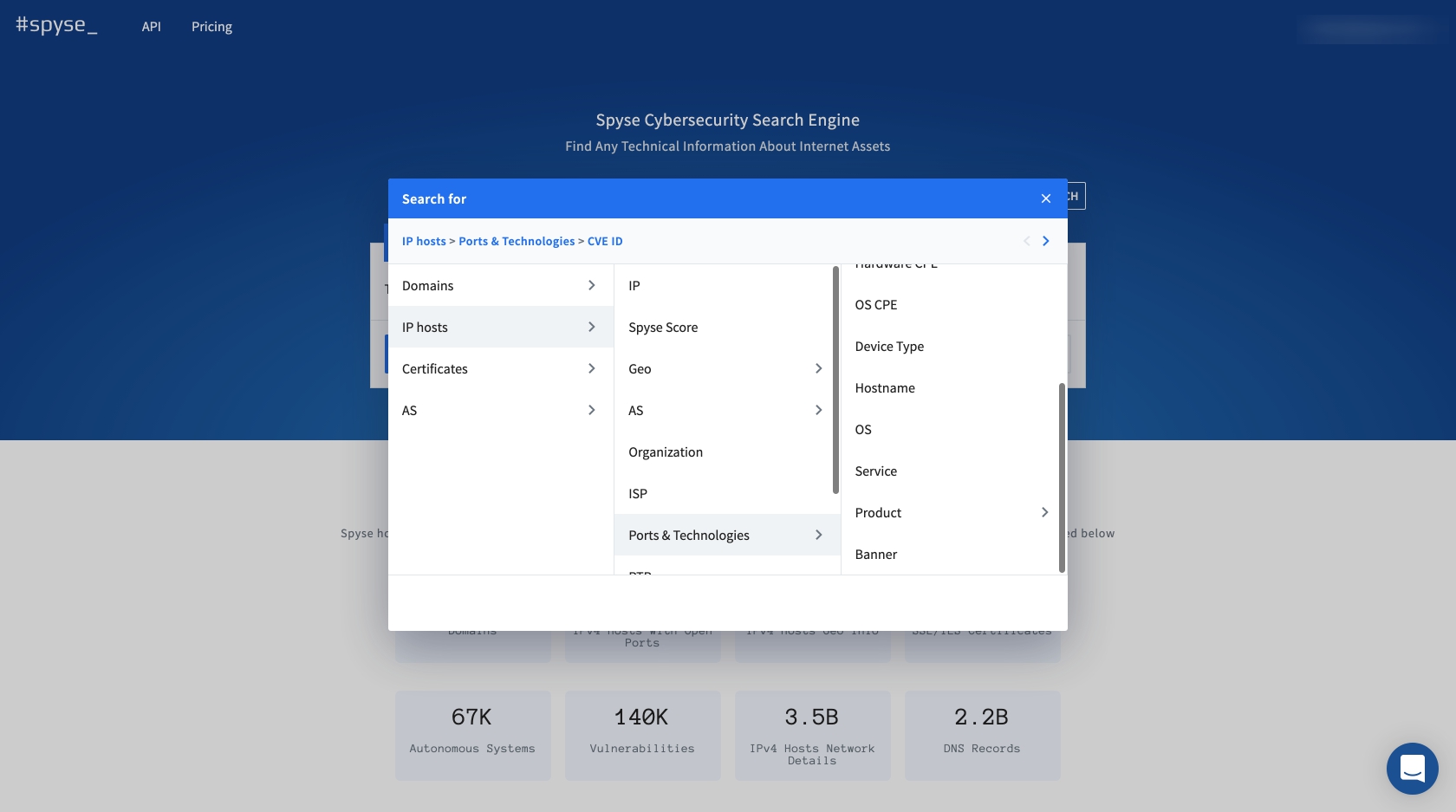
The Advanced Search is a live filter which helps sort big chunks of data as you’re browsing through the database. Users can apply up to 5 search parameters per query to extract very specific data that can’t be received with a simple search. For example: searching for ports users can obtain all open ports with specific CVEs, define products, applications, OS, and more in relation to some company.
To get quick information about open ports users may use Spyse’s port scanner that provides instant data without waiting for long scans.
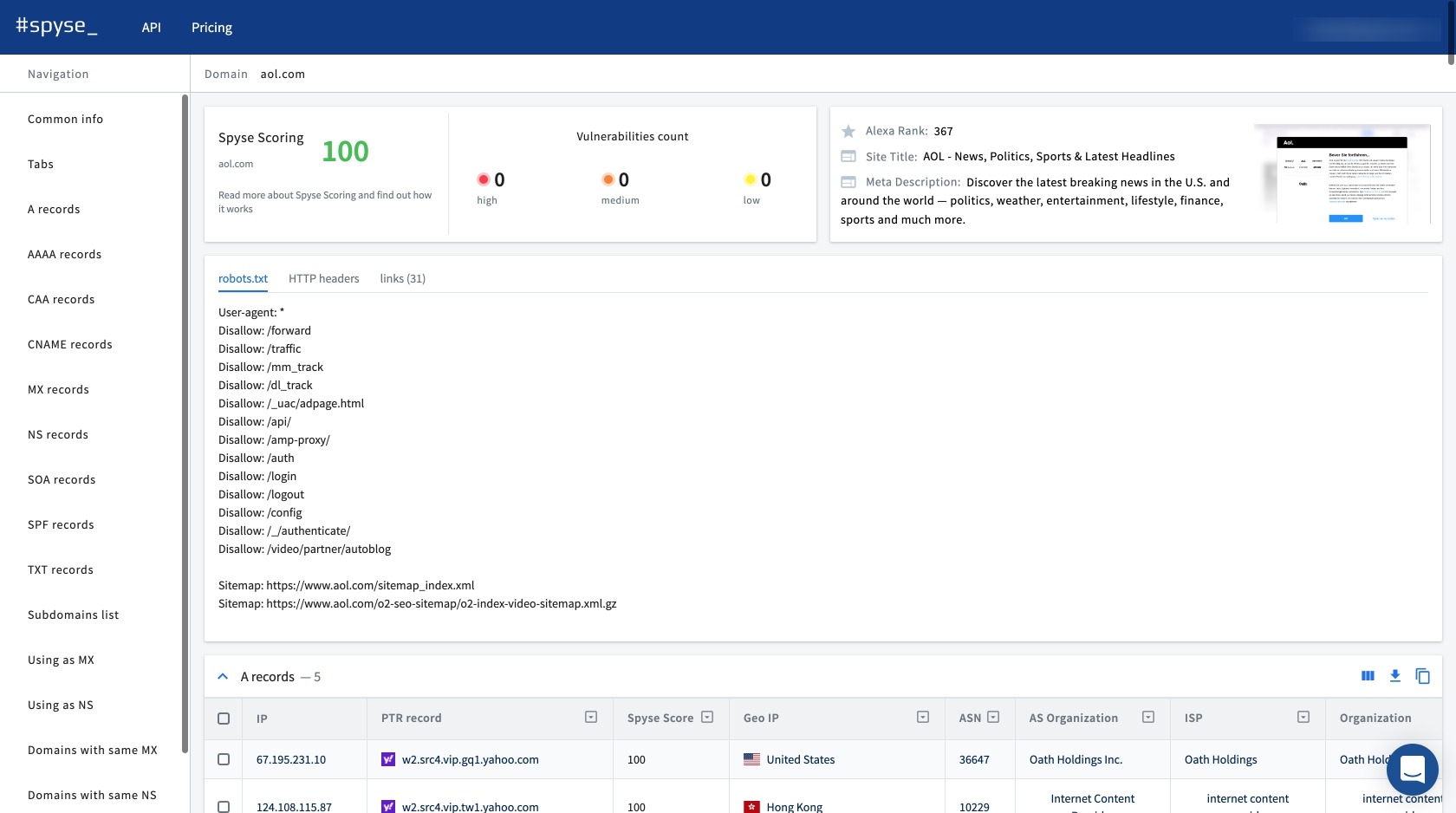
Spyse Scoring is another powerful feature which analyzes targets for vulnerabilities. It compares all information found by spyse scanners, and shows the level of security based on the rating of 0-100. Each found vulnerability is presented with expanded details that explains its severity, vector, dates and other info.
But it significantly improves when used in combination with the Advanced Search, allowing search by CVE IDs and the vulnerability score combining it with other search parameters for fascinating results.
Whom Spyse Was Made For
Using this search engine pentesters and bug bounty hunters will always remain invisible while seeking vulnerabilities, save money and time for their own scanning infrastructure and avoid the rate limits. It can also be used when other methods are rendered unavailable by contract or bug bounty agreement.
Overall, Spyse significantly improves the quality of specialists’ work and provides some new experience solving the daily routine tasks.
The post Spyse – Cybersecurity Search Engine for Quick Recon appeared first on The Crazy Programmer.
from The Crazy Programmer https://ift.tt/3gkpqoy
Comments
Post a Comment